| P e n T e s t » S c a n n i n g |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Economics Teacher: Bueller? Bueller? Bueller? |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Scanning and fingerprinting are extended forms of the reconnaissance phase of an attack or audit. Here, we attempt to detect live systems on the network, identify their OSes, as well as identify the services running on the network. Like Ben Stein in Ferris Bueller's Day Off, we can actively probe for information (Bueller? Bueller? Bueller?) and gather information based on the replies that we receive, or we can passively sit and listen for information that travels on the wire, thereby opportunistically building a picture of the network without sending out any data ourselves. Just as with the footprinting phase, our goal is to obtain a detailed blueprint of the network so as to be able to narrow the scope of the attack phases later on in our pen test. ICMP Yes, we're talking about Ping, that most prevalent network diagnostic tool. The Ping utility works by sending ICMP Echo Request (ICMP Type 8) messages to a target host. If the target responds with Echo Reply (ICMP Type 0) messages, it indicates that the target is reachable. Ping sweeps consist of ICMP Echo Requests sent to multiple hosts. A Ping sweep is one of the oldest methods of scanning a network, but it is a rather slow process, especially if the Ping sweep has been configured to test a large IP address range. Some network scanning tools such as scanrand, are able to speed up the process by using stateless TCP scanning instead.
Additional information that can be gleaned is the time taken for the packets to travel back and forth, indicating responsiveness and throughput. The OS of the target can sometimes be identified by the TTL (Time To Live) field. TTL is an 8-bit field in the IP header that indicates how many more hops this packet should be allowed to make before being dropped or returned. The remote host always sets the TTL field of its ICMP reply packet to a certain initial value, and the value is decremented as the packet passes through routers. The default initial value of the TTL field varies by OS.
In Unix, the Identifier and Sequence Number fields are used to identify echoes and replies when the Code field is zero. The Identifier field is set to the Process ID of the sending process. In Microsoft Windows systems, the ICMP Identifier field has a constant value, depending on the version of Windows. Therefore, it is possible to identify the different Microsoft operating systems passively when someone is using the Ping utility to query our machines. An in-depth look at ICMP's uses in OS fingerprinting can be found in ICMP Usage in Scanning v. 3.0, by Ofir Arkin.
ICMP Attacks Ping of Death - Ping of Death works by sending a Ping packet that is larger than the maximum IP packet size of 65,536 bytes. The default size of a ping packet is 64 bytes. Many OSes cannot handle anything larger than the maximum IP packet size. But if the packet is first fragmented, the fragments are small enough to be sent. When the target system receives the fragments, it will reassemble the oversized data packet. The size of the packet can result in a buffer overflow and cause the system to crash. Countermeasure: Apply vendor patches. Smurf Attack - A Denial of Service attack. Sends a lot of ICMP Echo Request traffic to the broadcast address of the subnet, with a spoofed source address (the address of the intended victim.) Most hosts on the subnet will reply to the spoofed source address with an ICMP Echo Reply. This could result in hundreds of hosts sending a huge amount of ICMP traffic to the intended victim. Countermeasures: Disable the forwarding of directed broadcast on all router ports (e.g. on a Cisco router, use no ip directed-broadcast), configure hosts to not respond to ICMP datagrams directed to broadcast addresses, use ingress filtering to prevent IP address spoofing (by checking the source address of a packet against the routing table to ensure the return path of the packet is through the interface it was received on.)Ping Flood - Another Denial of Service attack. An attacker (with substantially more bandwidth than the victim) overwhelms the victim with ICMP Echo Requests. If the victim responds with ICMP Echo Reply packets, it will consume outgoing bandwidth as well as incoming bandwidth. Countermeasure: Victim implements a firewall rule that drops ICMP Echo Requests. Port Scanning Portscan - Scan a single target host for all its open or listening ports. Portsweep - Scan multiple target hosts for one particular listening port. The speed of the portscan depends on the methodology. A slower port scanner will send a SYN packet to a target port and wait for a response. After the response is received, the port scanner repeats the process with the next port on the target. Faster portscanners such as scanrand do not follow this serialized scan process. They send out SYN packets to multiple ports on multiple targets simultaneously and wait for the responses. When we know which of the 65535 ports on a host are open, we can extrapolate and say we have a reasonable idea of the services running on that host. (This assumes that the services are using their default ports.) 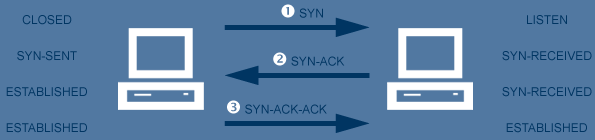 TCP Scans - The simplest port scan is a connect scan. The port scanner sends a SYN (synchronize) packet to the target. If the target port is open, the target completes the TCP three-way handshake, and the port scanner immediately closes the connection. A SYN scan a.k.a. half-open scan is the most popular form of TCP scanning. The port scanner sends a SYN packet to the target. If the target port is open, it will respond with a SYN-ACK packet. The port scanner responds with a RST (reset) packet, closing the connection before the handshake is completed. UDP Scans - UDP is a connectionless protocol, so we cannot reliably provoke the target to respond as we did using the connection-oriented TCP protocol. There are a few possibilities, though. If a UDP packet is sent to a port that is not open, the system will respond with an ICMP port unreachable message. If there is no response, we can extrapolate that the target port is open. (This method is thwarted by a firewall that blocks responses, thereby making us think that all ports are open.) A more reliable method is to send service-specific UDP packets (e.g. a DNS query) to the target, in hopes of receiving an Application Layer response. This method can be thwarted by configuring the service to not respond to probes. In any case, we are limited to a very few service-specific probes that are available. TCP and UDP Attacks TCP SYN Flood a.k.a. half-open attack - A Denial of Service attack that works by sending bogus TCP connection packets to the target host with a spoofed unreachable source address. The target replies to the spoofed source address. Naturally, there is no response. Connections are not completed. The target's connection request table fills up and it cannot handle legitimate requests. Countermeasures: Apply vendor patches that clear incomplete connection attempts. Configure IDS to identify TCP SYN traffic. Implement TCP SYN traffic rate limiting. Implement stateful inspection firewalls. The most effective countermeasure is SYN cookies, which delay allocation of resources until the source address has been verified. Land Attack - Works by sending a TCP SYN packet spoofed with the target's IP address and an open port as both source and destination addresses. The target will then endlessly reply to itself. Countermeasures: Apply vendor patches. Filter such poison packets with a firewall UDP Bombing - A UDP Denial of Service attack. Uses forged UDP packets to connect the echo service on one machine to the chargen service on another machine. The result is that the two services consume all available network bandwidth between them. Thus, the network connectivity for all machines on the same networks as either of the targeted machines may be affected. Countermeasure: Disable echo and chargen (and any other unused services). Filter UDP traffic on firewalls. UDP Flood a.k.a. Fraggle Attack - Another UDP Denial of Service attack. Very similar to Smurfing, except we use UDP packets. The attacker sends a huge amount of UDP Echo traffic to the subnet broadcast address with a spoofed source address. The source address is that of our victim. Countermeasures: Disable the forwarding of directed broadcast on all router ports (e.g. on a Cisco router, use no ip directed-broadcast), configure hosts to not respond to UDP datagrams directed to broadcast addresses, use ingress filtering to prevent IP address spoofing (by checking the source address of a packet against the routing table to ensure the return path of the packet is through the interface it was received on.)OS Fingerprinting OS Fingerprinting is the process of detecting the operating system that is installed on a remote host. We can do this in a number of ways, but the process usually revolves around the fact that different OSes (and different versions of an OS) respond differently to stimuli: ICMP - As detailed in the ICMP section above, different OSes respond with different values in the TTL field of the ICMP Echo Reply. Other ICMP fields, such as Sequence, also vary by OS. TCP / IP - Once again, the TCP/IP stacks of different OSes respond differently when probed. Nmap can probe for an OS fingerprint by sending out a sequence of TCP SYN packets to an open port on the target and waiting for the responses. Telnet - Banner grabbing possible by simply attempting to telnet to the target. HTTP - HTTP banner grabbing possible. Find out the web server platform. Send the target a HTTP Request and the look in the Server field in the HTTP Response header. Or you could always check Netcraft for info about publicly-accessible servers. Other data - Of course, instead of actively probing the target, you could just fire up a packet sniffer and opportunistically capture packets that may be sent from the target. NetBIOS broadcasts, ARPs and other miscelleneous traffic contain information that we can use to extrapolate the OS of the target. Heck, just look at the MAC Address in the packet (provided you are on the same subnet) and you can tell the manufacturer of the NIC. You may get lucky with a NIC that is used only on a particular type of computer and be able to narrow down the possible OS of the target. Useful Tools There are a gazillion network-mapping tools out there. Some tools are marketed as an aid to network monitoring or maintenance, while others are geared towards locating security flaws. Regardless of the marketing hooey, most of these tools function in very similar fashions. The big difference is usually the user interface. Thus, your choice of tool will probably depend on:
If you do decide to automate the process to some degree, these tools are especially useful for mapping a network:
Further Reading I recommend that you familiarize yourself with the following:
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||